A Developer's Guide to Git Undo Push Safely

We've all been there. That sinking feeling in your stomach the moment you realize you've pushed a bad commit. Maybe it's a bug, a half-baked feature, or worse, sensitive data. Your first instinct is probably to panic. Don't.
While a hasty fix can make things much worse for your team, this is a super common scenario and, thankfully, very fixable.
Choosing Your Undo Method Revert vs Reset
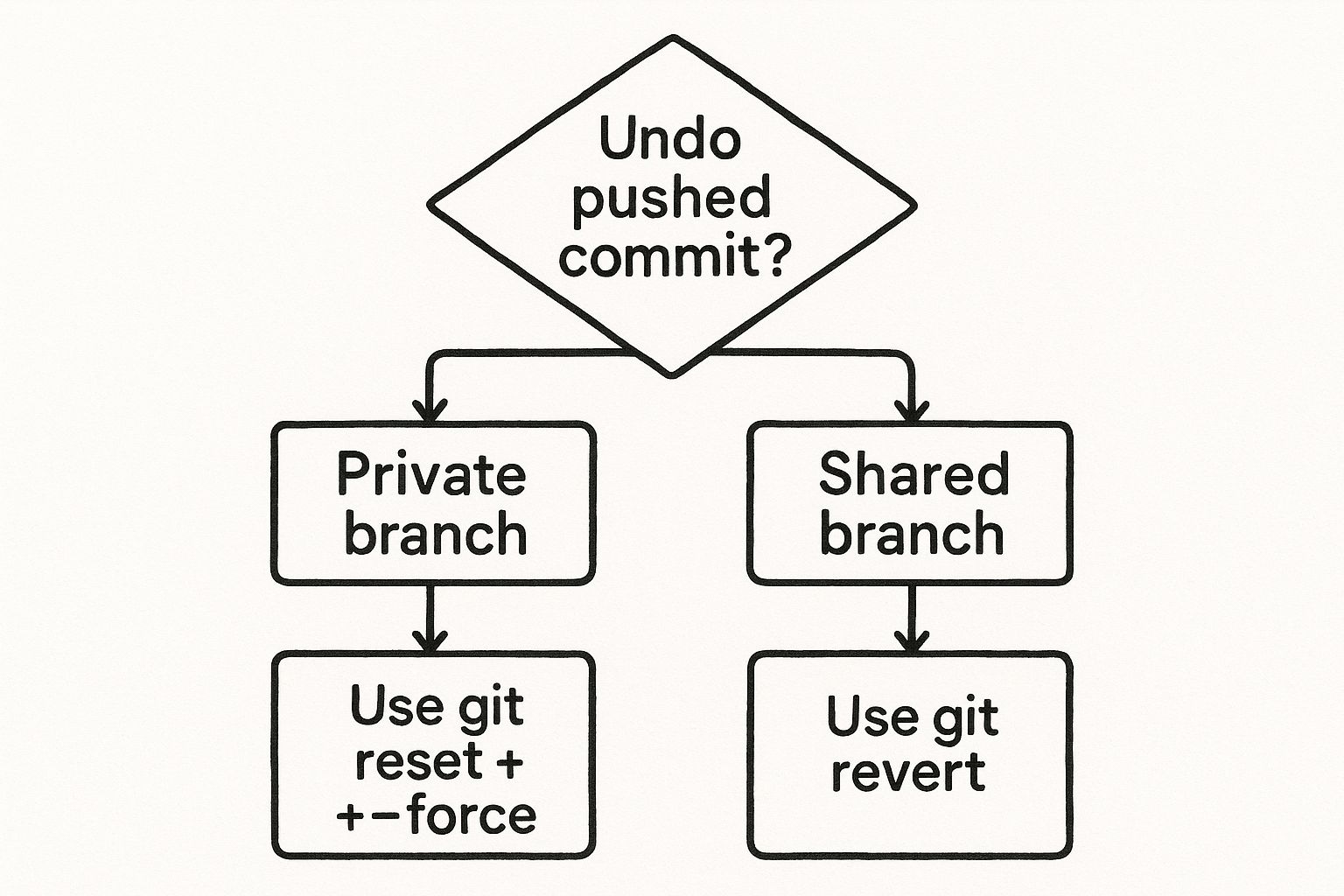
The right way to undo a push boils down to one simple question: has anyone else pulled your changes?
Answering that determines whether you need a non-destructive fix that plays nice with others, or a destructive one that rewrites history.
- Non-destructive (
git revert): This is your go-to for any public or shared branch. It works by creating a brand new commit that is the exact opposite of the one you want to undo. It’s clean, safe, and doesn't mess with the project's history. - Destructive (
git reset): This is the "it never happened" approach.git resetactually moves the branch pointer back to a previous commit, erasing the bad one from the timeline. It's powerful, but it’s a huge no-no on shared branches.
This decision is critical for team collaboration. Messing with the history of a branch others are working on is a recipe for disaster.
The main takeaway here? When you're working with others, you have to preserve a clean and consistent project history. That makes git revert the right choice almost every time.
To make it even clearer, here’s a quick breakdown to help you decide at a glance.
Choosing Your Undo Method Revert vs Reset
| Method | Effect on History | Best For | Safety Level |
|---|---|---|---|
git revert |
Creates a new commit that undoes the changes. History remains intact and linear. | Shared branches (e.g., main, develop) where others have pulled changes. |
High. It's the standard, safe way to undo changes in a collaborative environment. |
git reset |
Moves the branch pointer, effectively erasing commits. This rewrites the project history. | Private or local branches where you are the only one working on them. | Low. Extremely risky on shared branches, as it causes history divergence for teammates. |
This table should be your quick reference. When in doubt, always default to the safer option.
Why Reverting Is The Default Safe Choice
When you’re working on a public repository, rewriting history can cause chaos. That's why git revert is the gold standard. It creates a new commit that simply negates the changes from the bad one. The original commit is still there, but its effects are canceled out.
This approach became the norm as collaborative platforms like GitHub took off and millions of developers started working together on open-source projects. You can find more detailed examples on how to undo pushed commits with Git on GeeksforGeeks.
A revert is like an apology in your project's history. It says, "Oops, I made a mistake here," and then adds another entry showing how you fixed it. A reset tries to pretend the mistake was never made, which just confuses everyone who already saw it happen.
When you're working on a team, keeping the project history clean and understandable is everything. This is exactly why git revert is the go-to command for undoing a commit that's already been pushed. It's the professional standard.
Unlike other commands that rewrite history (we're looking at you, git reset), git revert takes a much safer, more transparent route.
Instead of just pretending a bad commit never happened, git revert creates a brand new commit that does the exact opposite of the one you want to undo. It's like finding a mistake in an accounting ledger; you don't erase the error. You add a new transaction that corrects the balance. This keeps the entire history intact, giving you a clear, auditable trail of what happened and when.
This approach is mission-critical. Why? Because it avoids the absolute chaos that happens when you rewrite the history of a branch that your teammates have already pulled down. A forced push after a git reset creates divergent histories, leaving everyone else on your team with confusing, painful merges to sort out.
Finding and Reverting The Problem Commit
Let’s walk through a scenario I've seen a hundred times: you've just pushed a commit, and a minute later, you realize it completely breaks the build. The CI/CD pipeline is screaming red alerts, and you need to fix it—fast—without tripping up anyone else.
First thing's first: you need to find the commit hash of the troublemaker. The easiest way is to peek at the recent project history using git log.
git log --oneline -n 5
This handy command gives you a quick, clean list of the last 5 commits. Once you spot the one that's causing the problem, copy its unique commit hash (that short string of letters and numbers). Let's say the bad commit is a1b2c3d.
With the hash in hand, the revert itself is dead simple.
git revert a1b2c3d
Git will then pop open your default text editor, asking you to write a commit message for this new revert commit. It'll suggest something like, "Revert 'Fix user login button styling'".
It's a best practice to add your own context to this default message. Briefly explain why the commit is being reverted. A clear message like "Reverting this commit because it broke the user authentication flow on mobile devices" is incredibly helpful for future developers.
Once you save the message and close the editor, Git creates the new commit. All that's left is to push it up to the remote repository.
git push origin main
And just like that, the problematic changes are reversed on the remote branch, the build goes green again, and your team's history remains consistent and conflict-free. This whole process is transparent and safe for everyone involved. For a deeper look at this command, our guide on how to revert a Git commit after a push has even more examples.
The Benefits of a Linear History
Using git revert ensures your project's history stays as a single, linear timeline of events. This is something highly valued in professional dev shops for a few key reasons:
- Auditability: Every single change, including the corrections, is documented. This is invaluable for code reviews, bug hunting, and just understanding how the codebase has evolved over time.
- Safety: You completely sidestep the danger of overwriting a teammate's work or forcing them into a nightmare of complex rebase operations to fix a divergent history.
- Simplicity: Your teammates can just
git pullthe latest changes and keep working. No one has to perform any complicated local repository surgery.
By choosing git revert, you're not just fixing a bug. You're being a good teammate and upholding a collaborative workflow that respects everyone's time and effort. It is the definitive safe way to git undo push in a shared environment.
When to Reach for the Powerful Git Reset Command
While git revert is the professional standard for anything on a shared branch, sometimes you just need a commit to completely disappear. This is where git reset comes into play. Think of it like a chainsaw—incredibly effective in the right hands, but an absolute disaster if you don't know what you're doing.
The golden rule here is simple: only ever use git reset on branches that you have not shared with other people.
Imagine you're deep into a new feature on your own private branch. You've made a few commits, maybe even pushed them to your remote backup, and then you realize the last commit was a total mistake. Since nobody else has pulled this branch, you can safely rewrite its history without throwing your team's work into chaos.
Understanding the Different Reset Modes
Not all resets are the same. Git gives you three main modes—--soft, --mixed, and --hard—each dictating what happens to your files after the history is rewritten. They range from least to most destructive.
--soft: This mode just moves theHEADpointer back to an earlier commit. It leaves both your staged changes and your working directory completely untouched. It’s perfect when you want to bundle your work differently, like squashing a few small commits into a single, more meaningful one.--mixed: This is the default setting forgit reset. It movesHEADand also resets the staging area (the index), but it leaves your actual working files alone. The changes from the commits you just undid will now show up as unstaged modifications.--hard: Here’s the most powerful—and dangerous—option. This mode movesHEAD, clears the staging area, and completely overwrites your working directory to match the commit you're resetting to. Be warned: any uncommitted changes will be gone for good.
For undoing a pushed commit on a private branch, git reset --hard is usually the most direct route. It cleanly wipes the commit and its changes from your local repository. If you're dealing with more complex scenarios, you can learn more about how to reset your branch to the remote HEAD.
The Safer Way to Force Push
After you run a git reset --hard, your local branch's history is now out of sync with the remote. You'll need to force push to get them aligned. But just running git push --force is a risky move. It blindly overwrites the remote branch. If a teammate somehow pushed a change in the seconds before you did, you'd wipe out their work without a single warning.
A much, much safer way to do this is with git push --force-with-lease.
git push --force-with-lease is a protective command. It first checks if the remote branch has been updated by someone else since you last fetched it. If it has, the push gets rejected, saving you from accidentally bulldozing a colleague's contributions.So, let's say you want to get rid of that very last commit you pushed. The process looks like this:
- First, remove the commit from your local history:
git reset --hard HEAD~1 - Then, safely force push your updated history:
git push --force-with-lease
This one-two punch is the cleanest, most responsible way to handle a git undo push on your private branches. You get the pristine history you want without the high risk of disrupting your team.
Still, the danger of misusing force pushes is very real. A 2022 GitLab survey found that about 38% of Git users have run into problems from overwriting pushed commits. Worse, 75% of those incidents led to major merge conflicts and project downtime. It's a stark reminder of why using commands like --force-with-lease and setting up branch protection rules is so critical for any team.
Oh, the cold sweat moment. You've just pushed a commit and see it plain as day: an API key, a password, some other secret staring back at you from the remote repo. This isn't just a mistake; it's a full-blown "drop everything" security incident.
Let’s be crystal clear: git revert or git reset will not save you here. Those commands are like putting a band-aid on a broken leg. They only affect the tip of your branch, leaving the sensitive data buried deep in the commit history, a ticking time bomb for anyone who knows where to look.
This is a code red. It calls for a much more radical solution: rewriting the repository's history to surgically remove every trace of that sensitive data. Standard Git commands aren't built for this kind of operation. You need to bring in the big guns.

The Right Tools for History Rewriting
For a critical task like this, a couple of powerful utilities are the go-to choices in the development community. They're designed specifically to scan and scrub your entire project history.
- BFG Repo-Cleaner: A fast and straightforward tool written in Scala. BFG is fantastic at removing chunky files and, more importantly for us, passwords or other text strings. You just tell it what to find, and it obliterates it from your Git history.
git filter-repo: This is the modern, officially recommended successor to the oldgit filter-branch. It’s incredibly powerful and flexible, letting you rewrite history in all sorts of complex ways, including scrubbing specific files or text.
Be warned: using these tools is a major move. When you rewrite history, you're changing the commit hashes for the affected commits and every single one that came after them. This creates a massive ripple effect, potentially breaking CI pipelines, automation, and any audit trails that depend on those original commit IDs.
This cleanup isn't a solo mission. It's an emergency response that demands immediate and clear communication with your entire team. Everyone has to be on the same page to coordinate the cleanup and—crucially—prevent someone from accidentally pushing the compromised history right back into the repo.
Your Emergency Response Plan
The moment you spot exposed data, the clock starts ticking. You need a clear, actionable plan to contain the damage and sterilize the repository.
- Invalidate the Credentials. Now. Before you even type
git, your absolute first step is to revoke the leaked key, change the password, or disable the credential. Assume it's already been compromised. Don't wait. - Alert the Team. Tell everyone what happened. They need to stop all work, especially pushing new commits, until the repository is clean. This prevents them from re-introducing the sensitive data from their local copies.
- Rewrite History. Use a tool like BFG or
git filter-repoon a fresh clone of the repository to scrub the data. Follow the documentation for your chosen tool to the letter. - Force Push the Clean History. Once you've double-checked that the data is gone, you’ll have to force push the rewritten history to all branches on the remote. This overwrites the old, dirty history. Yes, it's a
push --force. - Coordinate with Teammates. Instruct everyone to fetch the new, clean history and rebase any local work they have. They must not merge their old local branches; doing so could re-contaminate the entire repository.
It’s a disruptive process, but absolutely necessary. Security teams will tell you the risk of re-contamination is incredibly high if just one developer pushes an old local copy. Despite the hassle, as of mid-2024, nearly 20% of enterprise repositories with documented data leaks have had to perform a full history rewrite. You can find more detailed guidance on removing sensitive data in GitHub's official documentation.
Look, knowing the right git commands to undo a push is only half the battle. Git is fundamentally a collaboration tool, and if you're not communicating, you're creating chaos for everyone else.
The second you force push or revert something on a shared branch, your next move shouldn't be in the terminal. It should be in your team's Slack or Teams channel.
A quick heads-up like, "Hey team, just reverted commit b4d451a on develop because it was breaking the build," saves everyone a massive headache. It stops your teammates from pulling down the bad code and building their new work on top of a broken foundation.
Lock It Down with Protected Branches
Of course, the best way to fix a bad push is to stop it from ever happening. That's exactly what protected branches are for. On platforms like GitHub and GitLab, you can set up rules for your most important branches, like main or develop.
It’s a game-changer. You can set up protections to:
- Block force pushes entirely: This is your silver bullet. It makes accidentally rewriting history on a shared branch impossible.
- Require pull request reviews: Make sure at least one other person lays eyes on the code before it gets merged.
- Mandate passing status checks: Don't even think about merging if the automated tests and CI checks haven't passed.
Setting up branch protection is the single most effective proactive step you can take. It hardens your repository against the most common (and costly) human errors. What could have been a fire drill becomes a non-event.
Think of branch protection as the guardrails on a highway. It doesn't stop you from driving, but it does an excellent job of preventing you from accidentally veering off a cliff. It's a simple, powerful safety feature.
Build Better Team Habits
Beyond the technical guardrails, your team's day-to-day habits are your best line of defense.
Working in feature branches should be non-negotiable. This simple practice keeps your main branches stable and clean because all the messy, in-progress work happens in an isolated space. A mistake on a feature branch is a minor blip. A mistake on main can bring the whole team to a grinding halt.
Finally, lean into thorough code reviews. Seriously. A second set of eyes is unbelievably good at spotting bugs, logic flaws, or even secrets you accidentally left in the code before it gets merged. A team that prioritizes solid reviews will find that "undoing a push" goes from a regular firefighting exercise to a rare, once-in-a-blue-moon exception.
Common Questions About Undoing a Push
Even when you know the right commands, some situations can still leave you scratching your head. Let's walk through some of the most common questions developers face when they need to undo a git push and clean up the project history.
What If Someone Already Pulled My Commit?
This is the big one. The answer here completely changes your game plan. If there's even a chance someone has pulled the branch you need to fix, you should always use git revert. Seriously.
Trying to use git reset and then force pushing will rewrite history on the remote server. For anyone who already has the old version, this is a nightmare. Their local repository will now be out of sync with the remote, leading to a tangled mess of merge conflicts that are a huge pain to sort out.
Communication is your best friend here. In the very rare case you absolutely must reset a shared branch, you have to talk to every single developer on the team. They need to know exactly how to handle the history change on their end. If you can't do that, just stick to revert.Can I Undo a Merge Commit?
Yep, and it happens more often than you'd think. You can safely undo a merge using git revert, but the command is a little different than reverting a regular commit.
You have to tell Git which parent from the merge you want to keep as the "mainline." You do this with the -m flag.
git revert -m 1
In this command, -m 1 tells Git you want to preserve the history of the first parent—that’s the branch you merged into. This creates a new commit that effectively backs out all the changes brought in by the merge. It's so much safer than trying to reset a merge.
Is Force Pushing Ever Okay?
Using git push --force on a shared branch is almost always a terrible idea. It’s a sledgehammer that just overwrites the remote branch, and it can easily wipe out a teammate's work without any warning.
There’s a much safer way: git push --force-with-lease. This command adds a critical safety check before it does anything. It first verifies that no one else has pushed new work to the remote branch since you last pulled. If the remote has changed, the push gets rejected, saving you from accidentally overwriting their commits. It’s the only responsible way to force push.
And if you ever find yourself in a panic trying to recover a commit that got lost after a bad reset or rebase, the reflog is your safety net. We have a detailed guide that shows you how to use Git's reflog to find a lost commit.
At Mergify, we build tools to make your whole development workflow smoother and safer. Our Merge Queue prevents broken builds and keeps your main branch stable, which means you won't have to deal with these stressful "undo" scenarios nearly as often. Learn how Mergify can streamline your team's code integration.