Mastering GitHub Code Ownership
Defining GitHub code ownership is all about assigning clear responsibility for different parts of your codebase to specific people or teams. This isn't just about playing the blame game when something breaks. It's about building a smooth, predictable process for code reviews, long-term maintenance, and quality control.
Think of it as giving every line of code a dedicated steward.
Why Clear Code Ownership Matters
In any development environment that's moving fast, ambiguity is your worst enemy. When nobody is quite sure who owns a particular service or module, pull requests can sit in limbo for days, just waiting for the right person to finally take a look. These are the kinds of bottlenecks that can bring an entire project to a screeching halt.
Without a designated owner, code quality inevitably starts to degrade. You'll see different developers applying their own styles or architectural patterns, which leads to a messy and fragmented codebase that’s a nightmare to maintain. Even worse, security vulnerabilities can easily slip through the cracks when there isn't an expert responsible for sensitive areas like authentication or payment processing.
The Strategic Value of Accountability
Establishing a clear ownership model turns that potential chaos into a well-oiled machine. It creates a culture of accountability where teams don't just write code—they own it, take pride in it, and feel empowered to make decisions. Collaboration suddenly becomes faster and way more effective because developers know exactly who to ping for questions about any part of the system.
The sheer scale of modern software development makes this essential. As of early 2025, GitHub hosts over 1 billion repositories and forks, with more than 150 million developers contributing globally. That's a staggering amount of complexity to manage. It’s why tools like GitHub’s CODEOWNERS file are so critical for assigning responsibility and ensuring quality across millions of lines of code. You can dig into more of these numbers in the full GitHub statistics report.
By defining ownership, you're not just assigning tasks—you're distributing expertise. This ensures the right people are reviewing changes, which directly improves the stability, security, and long-term health of your software.
Three Pillars of Effective Ownership
A really solid GitHub code ownership strategy is built on three core pieces that work in tandem. Each one plays a unique role in transforming your ownership policy from a document that gets ignored into an automated, enforceable system.
- The CODEOWNERS File: This is your foundation. It's a simple text file living in your repository that maps file paths to specific GitHub users or teams. It's the source of truth for who owns what.
- Branch Protection Rules: This is your enforcement engine. By protecting critical branches like
main, you can set a rule that requires an official code owner to approve any changes before a pull request can be merged. No exceptions. - Smart Automation: This is where tools like Mergify come in. They build on top of GitHub's native features to handle more complex workflows, like requiring reviews from multiple teams or automatically merging a PR once all the ownership checks have passed.
Crafting Your First CODEOWNERS File
Alright, let's move from theory to practice. This is where a GitHub code ownership strategy really starts to pay off. The CODEOWNERS file is the heart of this entire system, acting as a simple but powerful map that automatically points review requests to the right people.
Let’s build one from the ground up.
At its core, the file is just a plain text document living inside your repository. The syntax is super straightforward, and if you’ve ever used a .gitignore file, you’ll feel right at home. Each line has a file path pattern followed by one or more owners. An owner can be an individual GitHub user (@username) or, even better, an entire team (@organization/team-name).
This simple structure is what gives you such precise control. You're basically writing a set of rules that GitHub's pull request system will follow to the letter.
Defining Basic Ownership Rules
Getting started is as simple as creating the file and dropping in your first rule. One of the first things to decide is where this file should live. You’ve got three common options:
- The
.github/directory: This is the standard, and for good reason. It’s where I recommend you put it. This keeps all your repository's configuration files neatly tucked away in one place. - The root directory: Placing
CODEOWNERSin the root works just fine, and you’ll often see this in simpler projects. No harm in it. - The
docs/directory: This is a less common choice, but it can be useful if your only goal is to define ownership for documentation files.
Once you’ve picked a spot, you can start mapping paths. For instance, say you want to assign all documentation changes to a dedicated team. You’d just add a single line like this:
Documentation files
docs/ @my-org/docs-team
With that one rule, any pull request that touches a file inside the docs/ directory will automatically ping the docs-team for a review. Simple as that.
Here’s a pro tip I've learned from experience: always, always favor team-based ownership (@my-org/team) over assigning code to individuals (@username). This is a lifesaver. It prevents pull requests from getting stuck in limbo just because one person is on vacation or leaves the company.
Using Wildcards for Broader Patterns
You definitely don't have to list out every single file. The real power of the CODEOWNERS file comes from using wildcards (*) to match patterns, which keeps your rules both concise and scalable.
Imagine you want a specific team to own all the Go files in the project, no matter where they are. You could just write:
*.go @my-org/go-developers
That one line covers every .go file. What if you need something more specific, like all JavaScript files buried within your src/components directory? You could use this:
src/components/**/*.js @my-org/frontend-squad
That double asterisk (**) is a fantastic tool for matching files across any number of subdirectories. Just remember that GitHub processes these rules from top to bottom, and the last matching pattern takes precedence. This is critical. It means you should always place your most specific rules at the very end of the file.
Getting your CODEOWNERS file set up correctly is the first major step toward a more organized and efficient workflow. It has a direct impact on how quickly pull requests get reviewed and merged, a huge factor in keeping your development velocity high. And for teams really looking to optimize their merge process, the logical next step is understanding how tools like a GitHub pull request merge queue can eliminate those frustrating bottlenecks for good.
Turning Ownership into a Rule with Branch Protection
A perfectly crafted CODEOWNERS file is a great start, but let's be honest: on its own, it’s just a suggestion. It guides reviewers and points people in the right direction, but it doesn't actually stop anyone from merging a pull request without the right approvals.
To give your GitHub code ownership policy real teeth, you need to pair it with branch protection. This is what transforms your helpful guideline into an unbreakable rule.
The Power of Enforcement
Branch protection rules are a set of configurations you apply to your most important branches—usually main or develop—to prevent unwanted or unapproved changes. By flipping one specific switch, you make an approved review from a designated code owner a non-negotiable requirement for merging any pull request.
This simple flow is the foundation of any serious ownership strategy.
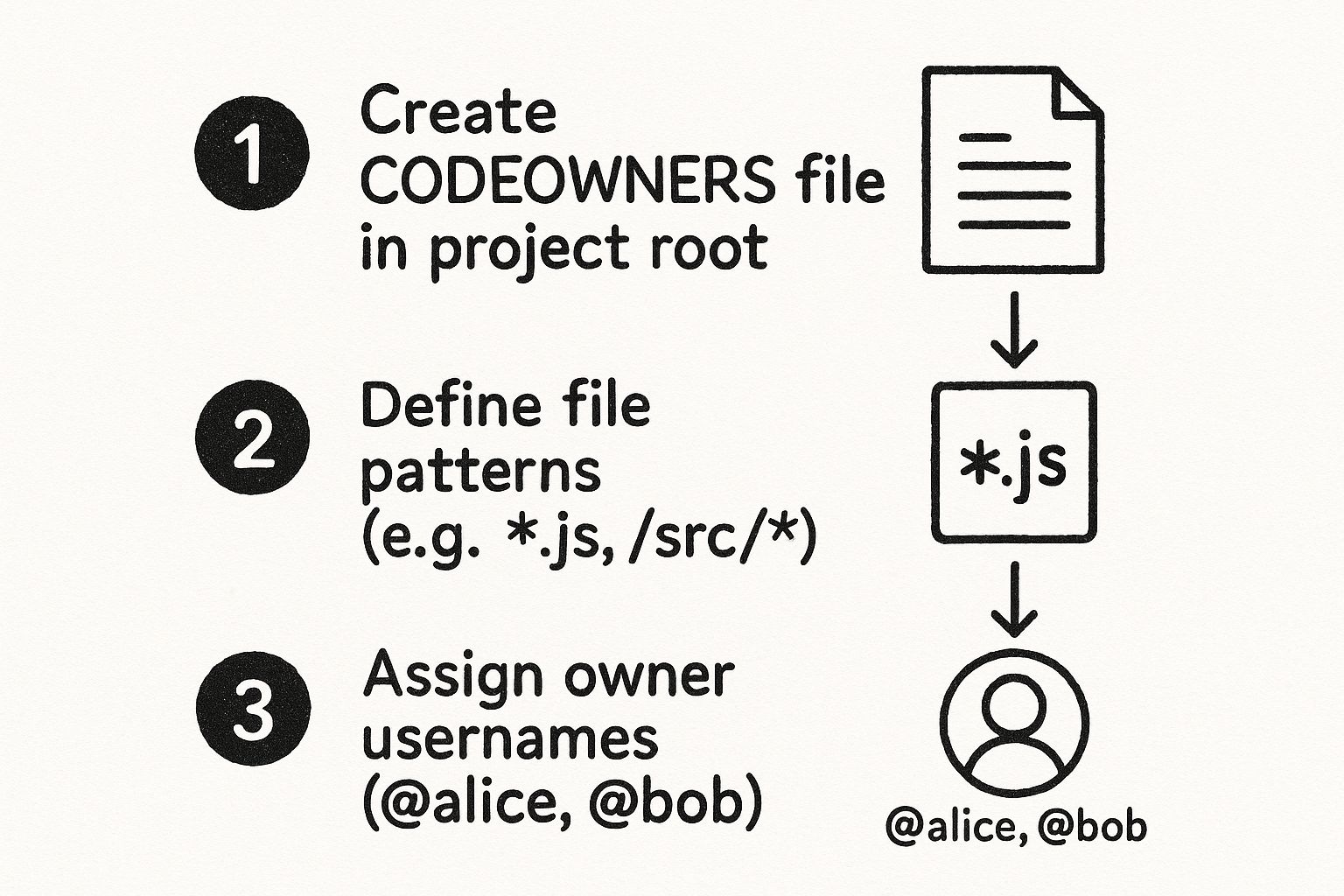
It all starts with creating the file, defining your patterns, and assigning owners. Then, you lock it all down.
Activating Mandatory Code Owner Reviews
Ready to set it up? Head over to your repository’s Settings and find the Branches section. From there, you'll add a protection rule for your target branch.
For this to work, you absolutely need two settings enabled:
- Require a pull request before merging: This is the baseline. It completely disables direct pushes to the branch, forcing every single change to come through a pull request where it can be properly reviewed.
- Require review from Code Owners: This is the magic button. Once you check this box, GitHub will automatically block a merge until the specific people or teams listed in your
CODEOWNERSfile have given their official approval.
This combination is a powerful safeguard. Imagine a junior developer accidentally trying to push a change to a critical API configuration file. Without this rule, their change might slip through. With it, the merge button stays grayed out until a senior member of the infrastructure team—the designated code owner—signs off.
Tying your CODEOWNERS file to branch protection is non-negotiable for serious projects. It's the mechanism that ensures your security, compliance, and quality standards are met on every single commit.The Real-World Impact
The value of this setup becomes crystal clear when the stakes are high. It's not a coincidence that around 90% of Fortune 100 companies use GitHub, where getting the right eyes on critical code is paramount.
To see the difference, let’s compare workflows with and without an enforced CODEOWNERS file.
CODEOWNERS vs. Manual Review Assignment
This table breaks down the practical improvements you'll see.
| Metric | Manual Review Assignment | CODEOWNERS + Branch Protection |
|---|---|---|
| Review Speed | Slow; requires manually finding and tagging the right person. | Fast; reviewers are automatically notified and assigned. |
| Security | Risky; PRs can be merged without expert approval. | High; mandatory review from designated experts prevents mistakes. |
| Accountability | Ambiguous; unclear who is ultimately responsible for a change. | Clear; ownership is explicitly defined and enforced in the codebase. |
| Developer Friction | High; developers waste time chasing down the correct reviewers. | Low; the process is automated, letting developers focus on coding. |
The takeaway is simple: automation removes bottlenecks and human error, leading to a more secure and efficient development cycle.
Think about your infrastructure-as-code (IaC) files, like Terraform or CloudFormation scripts. A mistaken change here could have immediate, catastrophic consequences for your production environment. By assigning these files to your SRE or DevOps team in CODEOWNERS and enforcing their review, you create a vital security checkpoint.
This is the essence of building a robust system. To get a deeper understanding of these protective measures, you can explore our complete guide on what GitHub branch protection is and why it matters.
Taking Your Review Workflows to the Next Level
Look, CODEOWNERS and branch protection are fantastic starting points. They give you a solid baseline for GitHub code ownership. But as your team and your codebase grow, you'll start to feel the edges. They can be a bit… rigid.
What happens when you need conditional logic? Or when a quick bug fix shouldn't have to jump through the same hoops as a massive new feature? This is exactly where automation tools become a game-changer.
Tools like Mergify are built to handle the sophisticated, dynamic workflows that native GitHub features just can't. They let you build an intelligent, automated system right on top of your existing ownership rules. The result is a pull request process that actually scales with you.
This screenshot gives you a sense of how an automation platform like Mergify can manage a merge queue and apply advanced rules on your behalf.
It's about having a central command center for your entire pull request lifecycle, going way beyond what you get out of the box with GitHub.
Building Smarter Ownership Logic
Let’s get practical. Imagine a pull request touches your critical payment processing logic. A standard CODEOWNERS file is great for pinging the @billing-team for a review. But what if you also want a mandatory sign-off from a senior architect for any change in that directory?
GitHub’s native setup doesn’t really have a clean way to handle that kind of multi-layered, conditional approval.
This is a perfect use case for a tool like Mergify. You can write a simple configuration that says:
- IF files in
src/payments/are changed... - AND the pull request is not labeled
trivial-refactor... - THEN require approvals from both
@my-org/billing-teamand@my-org/architects.
This is the kind of granular control that brings real efficiency. You’re applying the right expertise exactly when it’s needed, without bogging down routine changes with unnecessary red tape.
The goal of automation isn’t just to enforce rules—it’s to apply the right amount of process at the right time. Overly strict rules for minor changes create bottlenecks, while lax rules for critical code introduce risk. Smart automation finds the perfect balance.
Automating the Entire Pull Request Lifecycle
But true automation is so much more than just assigning reviewers. It’s about managing the entire journey of a pull request, from the moment it's opened to the second it's merged. The goal is to make the developer experience feel seamless.
For instance, a powerful automation engine can run a merge queue. Once your code owners have given their thumbs-up and all the CI checks have passed, the tool can take over. It will automatically queue the PR, rebase it against the latest main branch, run one final set of checks, and merge it safely.
This completely eliminates the dreaded "merge race," where multiple developers try to merge at once and end up breaking the build. It’s a huge win for productivity.
You can also craft distinct workflows for different types of changes:
- Bug Fixes: A PR with the
buglabel and an approval from the code owner could be automatically merged into ahotfixbranch. - New Features: A PR labeled
featuremight need an extra review from the product team and can only be merged during specific deployment windows. - Documentation: Simple changes to
.mdfiles? Maybe those can be set to merge automatically after just one approval from the@docs-team, skipping the long CI pipeline entirely.
This kind of tailored workflow acknowledges a simple truth: not all code changes are created equal. By automating these decisions, you free up your team to focus on what they do best—writing great code, not wrestling with merge conflicts or trying to remember complex review policies. This is how you build a pull request system that feels effortless, secure, and incredibly efficient.
Solving Advanced Ownership Challenges
As your projects get bigger and your teams grow, that simple CODEOWNERS file starts to feel a little… tight. The strategies that worked when you were a small team just don't scale, and establishing clear GitHub code ownership becomes a real headache. This is especially true in a monorepo, where dozens of teams might be pushing code into one massive repository.
When things get this complex, you need to think beyond the basics. A more sophisticated approach is required to handle organizational changes and technical complexity without grinding your entire development workflow to a halt.
Monorepos and Team-Based Ownership
The monorepo is a classic scaling problem. A single pull request can easily touch files owned by several different teams, creating a messy review process. The solution? Lean heavily on team-based assignments in your CODEOWNERS file.
Seriously, stop assigning critical paths to individual developers. Instead, create well-defined GitHub teams for each domain and give them ownership.
services/authentication/ @my-org/auth-teampackages/ui-components/ @my-org/design-system-squadinfra/terraform/ @my-org/platform-engineering
This small change has huge benefits. It prevents one person's vacation or sick day from blocking the entire team. It also makes ownership handoffs dead simple. When a developer switches teams, you just update their membership in GitHub—no more hunting through config files to change their username.
A common mistake I see is creating hyper-granular rules that map every single subdirectory to a different person. This just creates a maintenance nightmare. A good rule of thumb is to define ownership at the service or package level, mirroring your actual team structure.
Tiered Ownership for Critical Code
Let's be real: not all code is created equal. A tweak to a UI button is a world away from a change in your core payment processing logic. For this, you need a tiered ownership model, creating different layers of review for your most sensitive code.
While GitHub doesn't offer this out of the box, you can build it yourself with automation tools like Mergify. A tiered strategy might look something like this:
- Tier 1 (Standard): Most of your application code just needs one approval from the owning team (e.g.,
@feature-team). - Tier 2 (Sensitive): Any changes to shared libraries or core APIs? That'll require sign-off from both the owning team and a cross-functional group like
@staff-engineers. - Tier 3 (Critical): If someone touches security or infrastructure code (
/security/,/infra/), it should trigger mandatory approvals from specialized teams like@security-reviewersand@sre-leads.
This layered approach ensures the level of scrutiny always matches the level of risk. It transforms your ownership model from a simple notification system into an intelligent risk management framework, keeping your codebase stable and secure as you scale.
Common Questions About GitHub Code Ownership
As you start rolling out a GitHub code ownership strategy, you're bound to run into a few practical questions. It happens to everyone. Let's walk through some of the most common challenges I see and get you clear answers to sidestep those pitfalls.
What Happens If a Code Owner Is Unavailable?
This is the classic scenario: a pull request is completely blocked because the one person assigned as an owner is on vacation. It’s a huge bottleneck, but thankfully, the fix is simple.
The best practice here is to assign ownership to GitHub teams, not individuals.
For instance, instead of @sandra-dev in your CODEOWNERS file, you should use something like @my-org/backend-team.
This one small change means anyone on that team can jump in and approve the PR, keeping work flowing. For your most critical code, you can even assign multiple teams to build in extra redundancy. That way, you’re almost guaranteed someone will be around to handle the review.
Can I Have Different CODEOWNERS for Different Branches?
This is a frequent point of confusion. Can you set up branch-specific ownership rules?
The short answer is no. GitHub always looks at the CODEOWNERS file from the pull request's base branch, which is usually main.
What this means in practice is that the rules defined in your default branch apply to all pull requests targeting it. If you absolutely need different logic for, say, a release branch versus your main development branch, you’ll have to get creative with your repository structure or bring in an automation tool like Mergify to handle that advanced logic.
The rule of thumb is this: the last matching pattern in the CODEOWNERS file wins. If a file path matches multiple rules you’ve written, GitHub will only apply the one listed last. This makes the order of your rules critical—always put more specific patterns below general ones.How Does Rule Precedence Work?
So what happens when a single file matches a few different patterns in your CODEOWNERS file? How does GitHub decide which one to use?
It follows a dead-simple "last match wins" principle. The very last pattern in the file that matches a given file path is the one that determines the owner.
This makes the order of your rules incredibly important. You should always place your most specific, granular patterns after the more general, broad ones. Getting this right ensures your rules are applied exactly as you intend. This kind of attention to detail is a cornerstone of many GitHub code review best practices.
With Mergify, you can automate these complex ownership scenarios, creating dynamic and intelligent pull request workflows that go far beyond GitHub's native capabilities. Discover how Mergify can streamline your entire merge process.