What Is Static Code Analysis and How Does It Work
Ever had that sinking feeling when a seemingly tiny bug brings down your whole application in production? We all have. Static code analysis is your first and best line of defense against that nightmare.
Think of it as an automated, tireless proofreader for your software. It meticulously scans every line of your source code for potential bugs, security flaws, and style issues before you even try to run the program. It’s like a grammar checker finding typos in a document, but for your code.
What Is Static Code Analysis Anyway?
At its core, static analysis is a method of debugging code while it’s “at rest”—hence the term static. It doesn't need to execute the application. Instead, specialized tools analyze the code’s structure and logic to predict where problems might crop up. This proactive approach is the very foundation of Static Application Security Testing (SAST).
This "white-box" testing gives developers a blueprint-level view of their application, letting them spot foundational problems early in the development lifecycle. It’s a completely different beast from dynamic analysis, which tests the app while it's running. If you're curious about the contrast, it's worth exploring the differences between DAST and SAST in more detail.
To give you a quick snapshot, here’s a simple breakdown of what static code analysis is all about.
| Static Code Analysis At a Glance | |
|---|---|
| Aspect | Description |
| What it is | An automated process of analyzing source code without executing it. |
| Primary Goal | To find bugs, security vulnerabilities, and code quality issues early. |
| When it's used | During the coding and integration phases of the development lifecycle. |
| Methodology | "White-box" testing, meaning it has full access to the source code. |
| Analogy | A spell-checker for your code, catching mistakes as you write. |
This table shows just how integral this process can be. It's not just a fancy tool; it's a fundamental shift in how we approach software quality.
The First Line of Defense in Software Quality
By integrating static analysis directly into the development workflow, teams catch problems when they are cheapest and easiest to fix—right after the code is written. This “shift-left” philosophy is a game-changer for modern software development.
This early detection pays off in huge ways:
- Identifies Security Vulnerabilities: It can flag common security risks like SQL injection or buffer overflows before they ever reach a testing environment.
- Enforces Coding Standards: It ensures the entire team sticks to consistent style guides, making the codebase more readable and maintainable for everyone.
- Prevents Common Bugs: It catches nasty logic errors, null pointer exceptions, and resource leaks that could lead to crashes in production.
The real magic here is automating the tedious parts of code review. Instead of relying solely on human eyes to catch every single mistake, static analysis provides an automated safety net. This frees up developers to focus on what they do best: building great features.
A Growing Market Reflects Its Importance
The adoption of static code analysis isn't just a fleeting trend; it's rapidly becoming an industry standard. The global static code analysis software market was valued at approximately USD 1.1 billion and grew to USD 1.14 billion the following year.
Projections show this market expanding to USD 1.33 billion by 2029, a clear sign of the increasing reliance on these tools for building reliable and secure software. By embedding this practice into their process, development teams don't just write code; they build a foundation of quality, security, and maintainability from the very first line.
How Static Code Analysis Works Under the Hood
Static analysis might feel like a bit of a black box, but it's not magic. Its ability to spot errors without ever running the code boils down to a methodical, multi-step process.
Think of it like an automated detective meticulously examining a building’s blueprints for structural weaknesses before construction even starts. The tool breaks down your code into an understandable model, then applies a set of rules to pinpoint potential problems. The whole operation hinges on the tool's ability to first understand the code's structure and then trace every possible execution path. It doesn't guess; it systematically maps out the logic.
Parsing and Building a Code Model
The first thing any static analysis tool does is parse the source code. It reads every line and breaks it down into its basic components, almost like diagramming a sentence in English class to understand its grammatical structure.
From this, it builds an Abstract Syntax Tree (AST). An AST is a tree-like representation of your code that maps out its entire structure—variables, functions, loops, you name it. This tree becomes the foundational model for all the analysis that follows, allowing the tool to navigate the code's architecture programmatically. It’s like creating a detailed, organized outline from a sprawling document.
This infographic shows the high-level flow, from scanning the code all the way to delivering actionable feedback.
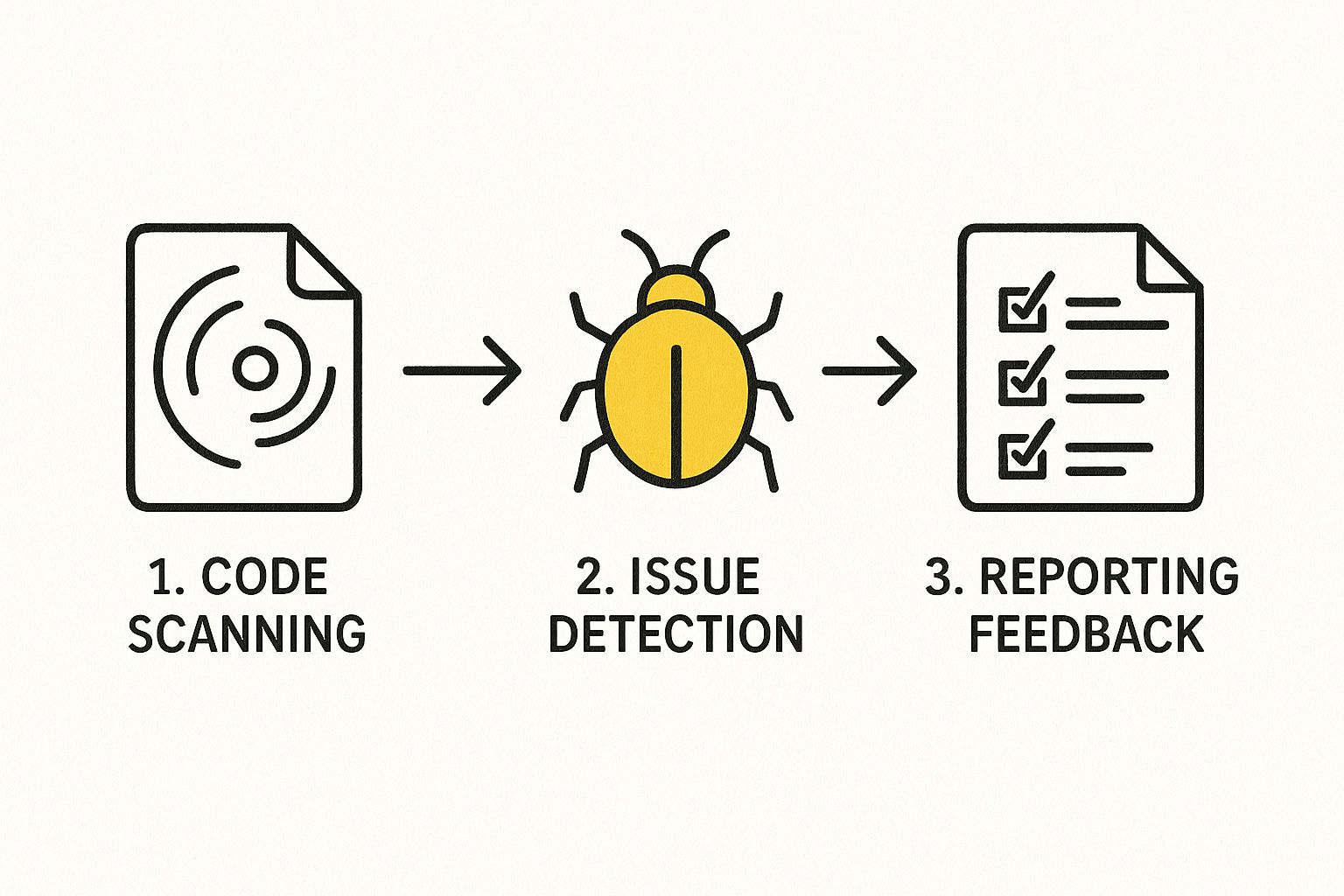
As you can see, the process is simplified into three core stages: scanning, detection, and reporting. It’s all about automated efficiency.
Tracing Every Possible Path
Once the AST is in place, the tool builds a Control Flow Graph (CFG). A CFG is basically a roadmap that charts out every possible path the program could take during execution. It maps out all the branches, loops, and decision points (like if-else statements).
This graph lets the analysis engine trace the flow of data and logic from start to finish, all without running the application. It's by analyzing these paths that the tool can spot issues like unreachable "dead" code or dangerous infinite loops.
By modeling both the code's structure (AST) and its potential behavior (CFG), static analysis tools get a complete picture of the software's internal workings, just from the source code alone.
Applying Rules and Finding Flaws
The final stage is where the real detective work happens. The static analysis tool applies a massive library of predefined rules and patterns to both the AST and the CFG. These rules cover a huge spectrum of potential problems.
This is where different types of tools really shine. Some tools, for instance, are all about code style and formatting. If you want to go deeper on that, you can learn more about what linters are and how they keep coding standards consistent.
Other tools focus on different kinds of issues, such as:
- Security Vulnerabilities: A rule might look for patterns that suggest an SQL injection, like when user input isn't properly sanitized before being used in a database query.
- Performance Bottlenecks: The tool can flag inefficient loops or clunky algorithms that might slow down the application under heavy load.
- Code Quality Bugs: Checks can identify things like potential null pointer dereferences, resource leaks, or variables being used before they're initialized.
- Style Inconsistencies: The analysis makes sure the code sticks to established team or project-specific formatting guidelines, which makes everything more readable.
When a chunk of code matches a problematic pattern, the tool flags it. It then generates a report detailing the issue, its exact location, and often a suggestion for how to fix it. This automated, rule-driven process gives developers immediate, actionable feedback, turning a complex analysis into a clear path to better code.
The Real-World Benefits of Static Analysis
Weaving static analysis into your workflow is so much more than a box-ticking exercise. It delivers real, measurable value that touches everything from developer happiness to your bottom line.
Think of it this way: would you rather proofread a book for typos before it goes to print, or recall thousands of flawed copies after they've already shipped? The first is a cheap, minor fix. The second is a logistical and financial nightmare.
Static analysis is your automated proofreader. It shifts quality control to the earliest, most cost-effective stage of development, and that changes everything.
Catch Bugs Before They Cost You
The most immediate win you'll see from static analysis is catching bugs early. Seriously early. Finding and fixing a bug during development is exponentially cheaper than dealing with one that’s escaped into production.
A simple null pointer exception caught by a developer at their desk might take a few minutes to sort out. No big deal.
But if that same bug makes it to production, it could cause system crashes, corrupt data, and tick off your customers. The cost suddenly explodes to include emergency dev time, frantic support calls, and a hit to your company's reputation. Static analysis tools are the safety net that catches these common—but critical—errors before they ever cause harm.
Static analysis transforms bug fixing from a reactive, high-stress fire drill into a proactive, low-cost routine. By identifying issues as code is written, it prevents technical debt from accumulating and ensures a more stable, reliable application.
This early intervention frees up your developers from endless debugging cycles. Instead, they can focus on what they do best: building new features and creating value.
Harden Your Security Posture Proactively
Right alongside quality, security is a massive reason to adopt static analysis. These tools come packed with rule sets specifically designed to sniff out common security vulnerabilities, like those on the infamous OWASP Top 10 list.
They can automatically flag risky coding patterns that might lead to SQL injection, cross-site scripting (XSS), or sloppy data handling.
And it’s incredibly effective. In federal security reviews, an estimated 72% of audited software vulnerabilities were traced back to code defects that a static analysis tool could have spotted. You can dig into the numbers and impact by exploring the full market research on static code analysis software.
By embedding security checks right into the development process, you make security a shared responsibility, not just something you worry about at the end. It's the essence of "shifting left"—hardening your app from the inside out.
Enforce Consistent Coding Standards
When you have a team of developers all working on the same codebase, consistency can go out the window fast. Different formatting styles, naming conventions, and patterns can turn the code into a hard-to-read mess.
Static analysis tools are the ultimate referees for your team’s coding standards.
They automate the enforcement of style guides, making sure every line of code follows the same rules. This consistency brings some huge advantages:
- Improved Readability: A uniform codebase is just easier for anyone to pick up and understand. This slashes onboarding time for new hires.
- Simplified Code Reviews: When a machine handles all the nitpicking over formatting and style, human reviewers can focus their brainpower on the tricky stuff—the logic and architecture.
- Easier Maintenance: Predictable code is much simpler to debug and change later on without accidentally breaking something else.
Ultimately, this automated enforcement creates a cleaner, more collaborative environment where the codebase stays manageable as it scales. It even acts like a built-in mentor, giving instant feedback that helps developers improve their skills on the fly.
Common Issues Uncovered by Static Analysis Tools
Think of static analysis tools as automated detectives for your codebase. But what kind of clues and culprits do they actually find? These tools are trained to spot everything from subtle performance drains to the kind of critical security flaws that can bring an application to its knees.
By understanding the types of issues they dig up, you start to see why they’re such a critical safety net in modern development. Let's break down the four most common categories of problems that static analysis brings into the light.
1. Critical Security Vulnerabilities
This is, without a doubt, the most important job for any modern static analysis tool. These tools act as your first line of defense, scanning for well-known vulnerability patterns that hackers absolutely love to exploit. It's like having an automated security audit that runs every time you push a commit.
Building a secure development lifecycle is a much bigger topic, and if you want to go deeper, it's worth exploring these essential software security best practices.
Common security landmines these tools will flag include:
- SQL Injection: This classic attack happens when unsanitized user input gets tossed directly into a database query, letting an attacker manipulate your database.
- Cross-Site Scripting (XSS): A nasty vulnerability that lets attackers inject malicious scripts into web pages that other, unsuspecting users will view.
- Insecure Data Handling: The tool flags things like passwords or API keys hardcoded directly into the source code—a huge, flashing red light for security.
For example, a tool might catch a piece of code that builds a query like this:String query = "SELECT * FROM users WHERE username = '" + userInput + "';"
This is a textbook SQL injection vulnerability just waiting to be exploited. The tool would immediately suggest using parameterized queries to neutralize the threat long before it ever has a chance to hit production.
2. Code Quality Issues and Bugs
Beyond security, static analysis is a beast at improving overall code quality. It catches common programming mistakes and logical errors that often lead to those frustrating, hard-to-reproduce bugs and unexpected crashes.
These are the kinds of problems that can easily slip past a human code reviewer who is focused on the bigger architectural picture.
Catching these foundational bugs early prevents them from evolving into complex, time-consuming problems later. It’s the difference between fixing a small crack in a foundation and rebuilding an entire wall.
Static analysis tools are particularly good at spotting:
- Null Pointer Exceptions: The tool can trace how a variable is used and identify paths where it might be accessed before it's properly initialized, preventing the infamous
NullPointerException. - Resource Leaks: It's great at detecting when resources like file streams or network connections are opened but never closed, which can slowly but surely exhaust your system's resources.
- Unreachable Code: It flags blocks of "dead code" that can never be executed, helping you clean up the codebase and reduce unnecessary clutter.
3. Performance Bottlenecks
A security breach is a catastrophe, but poor performance can be a silent killer for user adoption. Static analysis can identify inefficient coding patterns that might bog down your application, especially when it’s under heavy load.
It’s constantly on the lookout for algorithmic inefficiencies and resource-heavy operations that could be optimized.
For instance, a tool might identify a loop that makes a separate database call on every single iteration. That's incredibly wasteful. The fix is simple—fetch all the data at once before the loop begins—but finding it manually can be a pain. Spotting these patterns early saves a ton of performance-tuning headaches down the road.
4. Coding Style and Convention Inconsistencies
Finally, static analysis tools are the ultimate enforcers for your team's coding standards. A codebase with a mishmash of formatting, naming conventions, and patterns is a nightmare to read, maintain, and onboard new developers into.
These tools automate the "nitpicking" part of a code review, making sure everyone sticks to the agreed-upon style guide.
This includes checks for:
- Naming Conventions: Ensuring variables, functions, and classes are named consistently (e.g., camelCase vs. PascalCase).
- Code Complexity: Flagging functions that are way too long or have too many nested loops. These are tell-tale signs of logic that should be broken down and refactored.
- Formatting Rules: Enforcing consistent use of indentation, spacing, and brace placement across the entire project.
By letting a tool handle this, your developers can focus their brainpower on solving actual problems, not arguing about where a curly brace should go.
Choosing the Right Static Analysis Tool for Your Team
With what feels like a million static analysis tools on the market, picking the right one can be a real headache. Let’s be clear: there’s no single "best" tool. The perfect choice for a small open-source Python project is worlds away from what a massive enterprise needs for its sprawling, multi-language application.
The trick is to look past the brand names and flashy websites. You need a clear set of criteria to cut through the noise. This isn’t just about finding bugs; it’s about finding a genuine partner for your development process, one that fits right into your workflow and actually helps you ship better, more secure code.
It's no surprise that the demand for these tools is exploding. The global market for static code analysis software, currently sitting around USD 1.2 billion, is on a steep upward trajectory. Forecasts show it’s expected to more than double, hitting about USD 2.6 billion by 2032, a trend fueled by ever-growing software complexity and cybersecurity threats. You can dig into the numbers in the full market analysis on dataintelo.com.
Key Factors for Evaluating Tools
Before you even start looking at specific tools, you need to know what you’re looking for. Getting your priorities straight first will save you a ton of time later.
Here are the core areas to focus on:
- Language and Framework Support: Does the tool actually cover your entire tech stack? A tool that only understands 80% of your codebase is leaving some pretty big blind spots.
- CI/CD Integration: How smoothly does it plug into your pipeline? You need something that works seamlessly with your existing setup, whether that's Jenkins, GitLab CI, or GitHub Actions. Automation is the whole point.
- Rule Customization: Can you tweak the rules? The ability to turn rules on or off, or even write your own, is critical for cutting down the noise from false positives.
- Primary Focus: Is it built for security (SAST), code quality, or just enforcing style? Make sure the tool’s specialty lines up with what you care about most.
Open Source vs. Commercial Solutions
The market is pretty much split down the middle between powerful open-source options and feature-packed commercial platforms. Each has its pros and cons, and the right fit depends entirely on your team's budget, time, and expertise.
Open-source tools like SonarQube and ESLint are incredibly popular for a reason. They're flexible, backed by massive communities, and perfect for teams who don't mind getting their hands dirty with setup and maintenance.
On the other hand, commercial platforms like Veracode or Snyk often deliver more out of the box. They typically come with dedicated support, broader language coverage, and advanced security features tailored for large organizations with serious compliance demands.
Choosing between open-source and commercial isn't just about the price tag. It’s about the total cost of ownership. You have to weigh the time your team will spend on configuration and upkeep against the convenience of dedicated support and enterprise-grade features.
Here’s a look at the SonarQube dashboard, which does a great job of visualizing code quality metrics.
This kind of at-a-glance summary makes it incredibly easy to track your project's health and spot problems before they escalate.
A Practical Comparison of Popular Tools
To give you a better idea of what’s out there, I've put together a quick comparison of some of the most popular tools. This isn't an exhaustive list, but it should give you a solid starting point for figuring out which tools might be a good fit for your own evaluation.
| Comparison of Popular Static Code Analysis Tools | |||
|---|---|---|---|
| Tool | Type | Primary Focus | Key Strengths |
| SonarQube | Open-Source & Commercial | Code Quality & Security | Excellent dashboards, broad language support, and deep integration capabilities. |
| ESLint | Open-Source | Code Style & Quality | Highly configurable for JavaScript/TypeScript projects, great for enforcing coding standards. |
| Veracode | Commercial | Application Security (SAST) | Strong focus on security, detailed vulnerability reporting, and compliance features. |
| Snyk Code | Commercial | Developer-First Security | Scans for vulnerabilities in code and dependencies with a focus on actionable developer feedback. |
Ultimately, the only way to know for sure is to try them out. Pick a couple of top contenders and run them on a small but representative slice of your codebase. A hands-on trial run is the best way to see which tool gives you the most valuable feedback with the least amount of friction for your team.
Automating Code Quality in Your CI/CD Pipeline
The real magic of static analysis happens when you stop running it manually and weave it into the very fabric of your development process. By integrating these tools directly into your Continuous Integration (CI) pipeline, they transform from an occasional chore into an invisible, automated gatekeeper.
This move makes code scanning a seamless, mandatory check for every single change. No one has to remember to run a scan; the pipeline just does it. It's like having an automated quality inspector checking every brick before it’s laid.
Making Scans a Mandatory Gatekeeper
The whole point is to embed quality and security directly into your workflow, not treat it as an afterthought. When you configure your pipeline correctly, you can set up rules that automatically fail a build if the scan finds new, high-priority issues.
This creates a powerful, immediate feedback loop. It forces developers to deal with critical problems right away instead of letting them pile up as technical debt. This proactive approach is a cornerstone of modern development. To see how this fits into the bigger picture, check out our complete guide to building an effective CI/CD pipeline.
With automated enforcement, your quality standards stop being polite suggestions and become non-negotiable requirements for every commit. A failed build is a crystal-clear signal: this change doesn't meet the project's quality bar and needs more work before it can move forward.
This is how you prevent flawed or insecure code from ever hitting your main branch. It shifts the entire team's mindset from fixing bugs in production to stopping them from ever being written.
Enforcing Quality on Every Pull Request
Automation tools like Mergify take this even further by running these checks on every single pull request. Before a developer can even think about merging, the static analysis tool has to give the code a green light. Every PR becomes a quality checkpoint.
Here’s what that looks like in action:
- Pull Request Opened: A developer submits a PR with their proposed changes.
- Automated Trigger: The CI pipeline immediately kicks off the static analysis tool to scan the new code.
- Analysis and Reporting: The tool runs its checks and posts the results directly back to the pull request, usually as a status check or a comment.
- Automated Decision: If the scan uncovers critical issues, the PR is automatically blocked from being merged. If it passes, it's clear to proceed.
By making static code analysis an automated and mandatory step in your CI process, you build a powerful defense against bugs and vulnerabilities. This continuous, real-time validation fosters a culture of quality where secure, reliable code is the default, not the exception.
Got Questions About Static Code Analysis?
Let's wrap up by tackling some of the most common questions that pop up when teams first start exploring static analysis. We'll clear the air on a few frequent misconceptions.
Can Static Analysis Replace Manual Code Reviews?
Not a chance. Think of it as a powerful partner, not a replacement.
Static analysis is brilliant at catching the low-hanging fruit—common errors, security slip-ups, and style inconsistencies—all automatically. This frees up your human reviewers to pour their brainpower into what really matters: complex architectural decisions, tricky business logic, and algorithmic efficiency. These are the areas where human experience is absolutely irreplaceable.
Essentially, the tool handles the grunt work so your team can focus on the big picture.
Do These Tools Just Spam You with False Positives?
They definitely can, but modern tools are much smarter and more configurable than their older counterparts. If you're drowning in false positives, it's usually a sign that the tool's ruleset needs to be dialed in for your specific project.
You can almost always:
- Turn off irrelevant rules that just don't apply to your codebase.
- Tweak severity levels to bubble up the critical issues and quiet down minor suggestions.
- Mark specific warnings as "won't fix" for known exceptions in your code.
A little configuration upfront is the key. It transforms the tool from a noisy distraction into a genuinely valuable asset.
Isn't Static Analysis Just for Finding Security Flaws?
That’s a big part of it, but it’s only one piece of the puzzle.
Static code analysis tools are really about comprehensive code quality. They're just as good at spotting performance bottlenecks, enforcing consistent coding standards, and finding nasty bugs like null pointer exceptions or resource leaks that could bring down your production environment.
The main goal is to improve the overall health, reliability, and maintainability of your code for the long haul.
Ready to stop policing code quality and start automating your CI/CD pipeline? Mergify integrates powerful checks like these directly into your pull requests, ensuring every single merge strengthens your codebase. See how our merge queue and automation tools can save your team countless hours and keep bad code from ever reaching production. Start automating with Mergify today.